The analyst then compares the following results for port 22. C a private network of internal websites and other sources of.
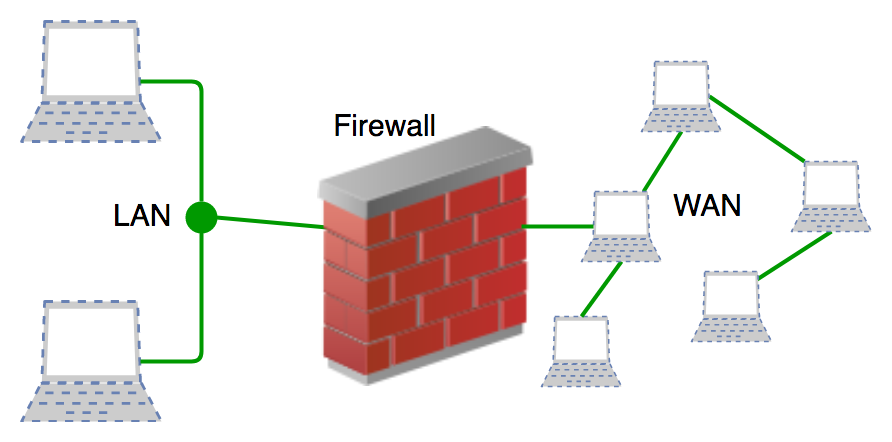
Introduction Of Firewall In Computer Network Geeksforgeeks
The analyst executes the following commands.

. All CS0-002 Questions A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewalls behavior and responses. Which of the following best describes a firewall. B a tool that searches Web pages containing the users search terms and then displays pages that match.
Operates at the OSI network layer. Which of the following BEST describes the. It sends traffic through another host.
Which of the following best describes an application-level firewall. Operates at the OSI session layer. A proxy installed between a firewall and a web server b.
A softwarehardware technology used to protect a network from outside attacks. Relies on algorithms to process application layer data. Operates at the OSI network layer.
A softwarehardware technology used to protect a network from outside attacks. Examines traffic for application layer protocols 2. A firewall is a system that protects a private network against unauthorized access.
A a software and hardware system that prevents outsiders from accessing a companys internal network B a tool that searches Web pages containing the users search terms and then displays pages that match C a private network of internal websites and other sources of information available to a companys employees D. A load balancing system that acts as a funnel point for traffic that is an ideal place to enforce policy and that is done through the firewall d. Examines traffic for application layer protocols x 2.
It safeguards the internal network by filtering incoming and outgoing traffic according to a set of criteria. It is based on peer working model. A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewalls behavior and responses.
A host-based firewall is a hardware firewall that protects a single endpoint device. It acts as a gateway for requests arriving from the client. It is typically run on the host system.
The analyst executes the following commands. Unauthorized users are prevented from accessing private networks connected to the Internet particularly intranets using firewalls. A a software and hardware system that prevents outsiders from accessing a companys internal network.
A firewall is a network segment off the firewall in which you put systems that require different levels of access than other network components. A host-based firewall is a hardware firewall that protects multiple endpoint devices. The analyst then compares the following results for port 22.
Which of the following statements best describes a firewall. It is based on Client - Server model. Operates at the OSI session layer.
A _________ firewall keeps track of the established connections passing through it. A firewall is a pass-through device that allows only certain traffic in and out. Which of the following BEST describes a firewall.
It is based on work group model. Which of the following best describes a packet-filtering firewall. 63 Which of the following BEST describes a firewall.
In general firewalls work by _____________. Which of the following best describes a proxy firewall. It checks only the IP and protocol.
A host-based firewall is a software firewall that protects multiple endpoint devices. Allowing only packets that pass security restrictions to be forwarded. Relies on algorithms to process application layer data.
A device that analyzes traffic based on destination address c. Which of the following best. Q4Which of the following best describes FireWall-1 model of operation.
Which of the following best describes a firewall. Which of the following types of firewall causes the largest reduction in the performance of the device on which it is instilled. A firewall is an external DNS server.
Which of the following best describes a network chokepoint. This is the best answer based on feedback and ratings. Which of the following best describes a circuit-level firewall.

What Is A Firewall Definition Key Components And Best Practices Toolbox It Security

This Picture Describes How Does The Internet Works In My Opinion This Is A Great Picture Because It Show How Internet Works Local Dating Sites Internet Dating

This Describes How The Networks Work With The Computers Technology Management Router Switch Pbx
0 Comments